Cov txheej txheem:
Video: Cov theem ntawm qhov xwm txheej teb yog dab tsi?

2024 Tus sau: Lynn Donovan | [email protected]. Kawg hloov kho: 2023-12-15 23:47
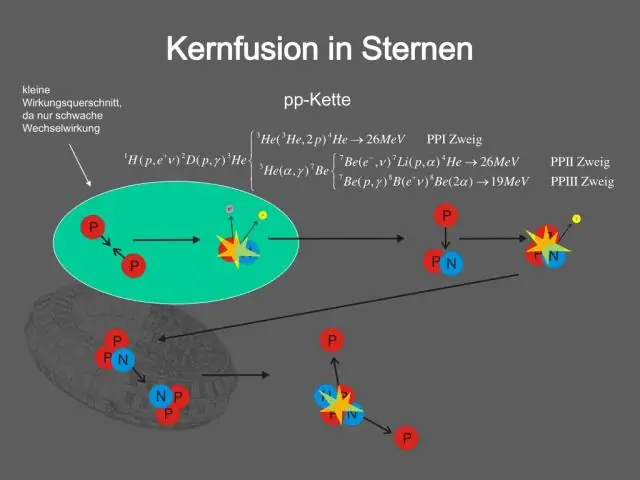
Qhov xwm txheej teb theem. Cov lus teb tshwm sim feem ntau raug muab faib ua rau theem; kev npaj , kev txheeb xyuas, kev tuav pov hwm, kev tshem tawm, rov qab los thiab cov lus qhia tau kawm.
Kuj tseem yuav paub yog, dab tsi yog cov theem ntawm qhov xwm txheej teb txoj kev txhim kho?
Deuble hais tias rau theem ntawm qhov xwm txheej teb uas peb yuav tsum paub txog yog kev npaj , kev txheeb xyuas, kev tuav pov hwm, kev tshem tawm, rov qab los thiab cov lus qhia tau kawm.
Tsis tas li ntawd, txheej txheem teb qhov xwm txheej yog dab tsi? Qhov xwm txheej teb yog ib txoj hauv kev los daws cov teeb meem thiab kev tswj xyuas tom qab ntawm kev ua txhaum cai ruaj ntseg lossis cyberattack, tseem hu ua IT xwm txheej , computer xwm txheej los yog kev ruaj ntseg xwm txheej . Lub hom phiaj yog los tswj qhov xwm txheej ntawm txoj hauv kev uas txwv kev puas tsuaj thiab txo lub sijhawm rov qab thiab cov nqi.
Ib yam li ntawd, tib neeg nug, dab tsi yog tsib kauj ruam ntawm qhov xwm txheej teb nyob rau hauv kev txiav txim?
Tsib Kauj Ruam ntawm Kev Teeb Meem teb
- Kev npaj. Kev npaj yog tus yuam sij rau kev ua haujlwm zoo.
- Kev Tshawb Nrhiav thiab Tshaj Tawm. Lub hom phiaj ntawm theem no yog saib xyuas cov xwm txheej kev nyab xeeb txhawm rau txhawm rau txheeb xyuas, ceeb toom, thiab tshaj tawm txog qhov xwm txheej muaj kev nyab xeeb.
- Triage thiab Analysis.
- Containment thiab Neutralization.
- Kev ua si tom qab xwm txheej.
Dab tsi yog 6 theem ntawm kev tuav pov thawj?
Lub rau lub kauj ruam yog kev npaj , kev txheeb xyuas, kev tuav pov hwm, kev tshem tawm, rov qab los thiab cov lus qhia tau kawm. Cov txheej txheem zoo sib xws kuj tau coj los rau hauv lub neej los ntawm NIST ntawm Computer Security Incident Handling Guide (pub.
Pom zoo:
Dab tsi yog qhov txawv ntawm qhov xwm txheej thiab qhov xwm txheej hauv ITIL?
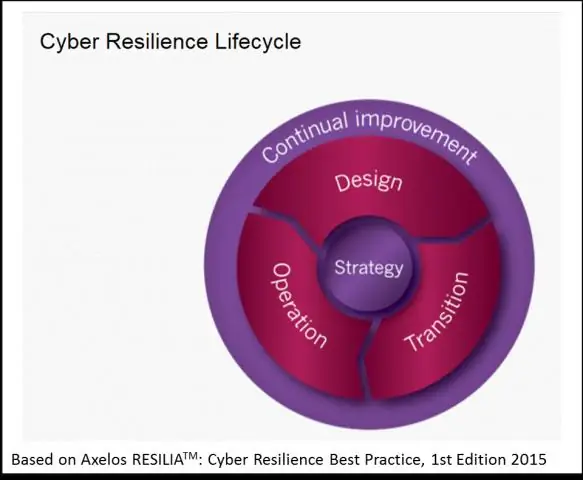
Qhov sib txawv ntawm cov xwm txheej thiab xwm txheej hauv ITIL Ib qho xwm txheej yog kev cuam tshuam uas tsis tau npaj tseg lossis txo qis hauv kev ua haujlwm ntawm IT kev pabcuam. Ib qho kev tshwm sim yog qhov hloov me ntsis hauv lub xeev ntawm cov kab ke lossis kev pabcuam hauv IT infrastructure
Dab tsi yog qhov txawv ntawm kev tswj qhov xwm txheej thiab kev tswj xyuas qhov xwm txheej loj?
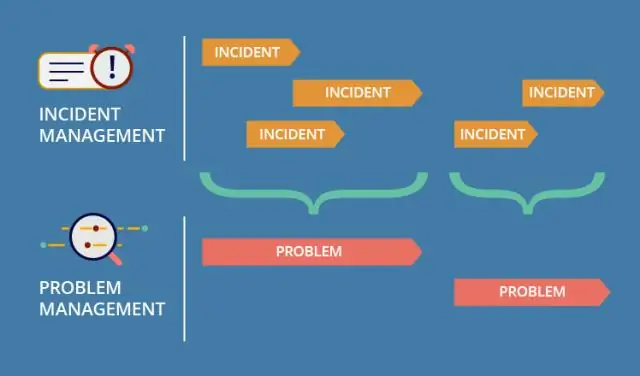
Yog li MI yog hais txog kev lees paub tias qhov xwm txheej ib txwm muaj thiab Kev Tswj Xyuas Teeb Meem yuav tsis txiav nws. Ib qho xwm txheej loj yog kev tshaj tawm ntawm lub xeev xwm txheej ceev. Ib qho xwm txheej loj yog nruab nrab ntawm qhov xwm txheej ib txwm muaj thiab kev puas tsuaj (qhov twg IT Service Continuity Management txheej txheem pib)
Dab tsi yog qhov txawv ntawm tag nrho cov ntawv tshaj tawm thiab ib nrab ntawm cov xwm txheej?
Rau cov khoom tsis sib xws hauv ib daim ntawv teev npe (raws li hauv Nieuwenstein & Potter's thwmsim, 2006) tag nrho daim ntawv tshaj tawm raug cuam tshuam los ntawm tag nrho cov khoom hauv ib ntu, qhov kev tshaj tawm ib nrab tsuas yog cuam tshuam tsawg kawg nkaus los ntawm tag nrho cov khoom, yog tias tsuas yog ob qho yuav tsum tau ua. qhia
Dab tsi yog cov kev pabcuam muab rau txheej txheej network los ntawm cov ntaub ntawv txuas txheej?
Cov kev pabcuam tseem ceeb yog hloov cov ntaub ntawv pob ntawv los ntawm txheej txheej network ntawm lub tshuab xa mus rau txheej txheej network ntawm lub tshuab txais. Hauv kev sib txuas lus tiag tiag, cov ntaub ntawv txuas txheej xa cov khoom ntawm lub cev thiab lub cev nruab nrab
Dab tsi yog qhov haujlwm ntawm OSI txheej txheej txheej txheej txheej txheem router ua haujlwm li cas?
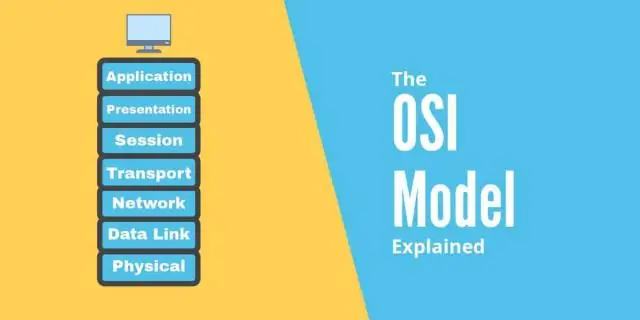
Hauv Cov Qauv Qhib Kev Sib Txuas Sib Txuas (OSI) kev sib txuas lus, txheej txheej txheej txheem nyob ntawm Txheej 5 thiab tswj kev teeb tsa thiab rhuav tshem ntawm kev sib txuas ntawm ob qhov kev sib txuas lus kawg. Kev sib txuas lus ntawm ob qhov kawg yog hu ua kev sib txuas
